Firewall Configuration Tips
Firewalls are probably the most user-unfriendly software among computer security applications, mainly because of the technicalities surrounding the detection of unauthorised access to your computer or unauthorised data transmission from your computer. This is why there are so many computers without a functional firewall, something that is a necessity these days. Firewalls can solve a lot of our basic problems like spam, denial of service attacks and even malware distributed by zombies. The term 'zombies' refers to normal home computers, workstations at an office, or even a server infected with malware. These zombie computers are used to distribute spam and malware and they are used as pawns in denial of service attacks.
A basic firewall works more or less like a spam filter. Most people are familiar with a spam filter and know how to use them, so think of the firewall as a spam filter for bad programs. You need to train your firewall, just like a spam filter, to block unwanted applications from accessing your computer and prevent unwanted activities from occurring on your computer. Many advanced firewalls contain a database, much like the virus definitions of an anti-virus application, but with the focus on the good applications instead of the bad ones. The firewall will know which applications can be trusted and any application not on that list will be blocked until the user explicitly allows it.
We know most people like free software and that is why most people prefer free firewalls. The only drawback is that these free firewalls do not have the fancy databases of the paid versions, so you will need to train the firewall to make it more effective and less annoying. We will explain 3 basic principles of firewall training by using ZoneAlarm as an example.
We are not going to guide you through the installation of ZoneAlarm, because the installation procedure of each firewall is different. Most firewalls have a step for scanning your computer during the installation process. This scan is done to determine which software applications are installed on your computer and which ones should be allowed by default. Free firewalls normally allow the most common and critical system applications and leave the rest of the training to the user.
Firewall Configuration Principle #1
If you are unsure whether you should allow the program access to the Internet or your local network, deny it temporarily. If the program runs without any loss in functionality, permanently deny the program access to the Internet, otherwise allow it.
The first basic principle of firewall configuration is perhaps the most important one. It is actually common sense and requires bit of increased concentration and awareness while using your computer. Directly after clicking on a shortcut on your desktop, or from the Start Menu or after any action you explicitly initiated, which can be anything from clicking with your mouse or pressing a key on your keyboard, you may receive a notification from your firewall, that a program is trying to access the Internet or your local area network. Now this is where common sense starts to play a role.
The notification will normally tell you the name of the executable file, trying to access the Internet. Most legitimate executable filenames are descriptive and you will be able to tell which program the firewall is referring to. But this is where most people get stuck. How do I know which programs should be allowed and which ones not? Most firewalls have a "Remember" setting, a little box that needs to be ticked to make the firewall remember your decision and not ask it again. In ZoneAlarm it's the "Remember this setting" option near the bottom of each Security Alert balloon. Whenever you are unsure whether you should allow a program access to the Internet or not, choose the Deny option, but do not tick the "Remember" setting. This will temporarily deny the program access to Internet. If you are able to use the program without any loss in functionality, then tick the "Remember" setting the next time you get a notification about this program, otherwise allow the program access to the Internet or network if you encounter some features not functioning anymore.
You should also ask yourself whether the application requires Internet access or not. A web browser will need to have access to the Internet to function properly, your anti-virus application needs Internet access to download updates and virus definitions, your e-mail client needs access to the Internet to download your e-mails and allow you to send e-mails. Almost every program uses the Internet these days, but you need to determine whether it is really necessary for the program to access the Internet. PDF readers, word processors, spreadsheet programs, presentation programs, image editors, multi-media players, CD burning software, printing and scanning software, video capturing software and many other programs, may all have merit in accessing the Internet, but is that really the truth? Nothing stops you from using your browser to download updates, why do they need to have access to the Internet, they can use your browser to send you to the appropriate update site. Most of these programs collect usage statistics, in other words, they monitor the performance of the software, but they may also monitor how and for what you are using the software. This information is then sent back to the software developers to help them improve the software. Most applications allow the user to disable this kind of monitoring, but many users do not understand it and leave it enabled anyway.
Many well-known and popular applications place start-up entries in our Windows registry without asking. These are the programs that start automatically each time you log into Windows. The largest majority of these applications are automatic updaters, running in the background all the time, periodically checking for new software updates. Imagine having an automatic updater for every program installed on your computer. You will end up having so many auto updaters in your system start-up that you will have enough time to make a cup of coffee while you wait for your computer to start up. Once your computer have loaded all these auto updaters in the memory you won't have any memory left for your other programs. Software developers are abusing this by placing a bunch of useless auto updaters on our computers, only wasting our time, memory and bandwidth.
Firewall Configuration Principle #2
If you did not initiate any action on your computer and your firewall reports that a program wants to access the Internet or your local network, deny it, unless you are familiar with the program.
If you suddenly receive a notification from your firewall out of the blue, be extremely careful what you allow. This is often a sign of malware lurking on your computer or someone trying to break through your firewall. However, note that there are occasions when this is not the case and it may well be a legitimate program trying to access the Internet. It is becoming harder to rely on the basic rule that automatic requests to the Internet are most of the times fraudulent, because software automation is becoming more popular by the day. ZoneAlarm has a feature called SmartDefence Advisor. It tells you whether you should allow or deny the activity reported by ZoneAlarm. This feature is not built into the firewall, but actually takes you to the ZoneAlarm website where you can find more about the details of the aforementioned activity.
Common sense plays an important role here as well. For instance if the firewall reports about a program trying to connect to a specific company's website, but you know you do not have any software of that company installed on your computer, you have more than enough reason to be suspicious. If the activity makes no sense, rather deny it.
Just like the first principle, it remains the safest option to deny the activity at first (DO NOT tick the "Remember" option) and monitor your computer for any loss in functionality after denying the action. For instance, your anti-virus might not update any more, your e-mail scanner may not appear when you download e-mails or your Internet may stop functioning. If you encounter any loss in functionality, reboot your computer and allow the action next time your firewall reports it.
Firewall Configuration Principle #3
Do not be afraid to ask for advice.
Short and sweet, but very important. If you allowed or blocked a specific activity reported by your firewall, and you are not sure whether it was the right decision, ask an expert to confirm whether you made the right choice. You do not want to end up reformatting your hard drive because of a problem that you may think is malware related, while the problem is actually caused by your firewall blocking an important system component or software application. Even worse, you do not want to allow a malicious program to gain access to your system, because that will only open the door to many other threats, rendering your firewall protection completely useless. Almost every firewall has a list of applications that are being allowed or blocked, but most users won't be able to find it and even if they do find it, they seldom know what to remove to solve the problem. So whenever in doubt ask an expert.
So basically in a nutshell, you need to have a little paranoia and a "trust no one" mindset when working with firewall training. You can identify most legitimate programs with a little trial and error, giving you better control over the applications running on your computer. It is essential to know what is going on in the background and a firewall makes that job so much easier.
Below is an example of a ZoneAlarm Security Alert highlighting of the most important details of the firewall notification.
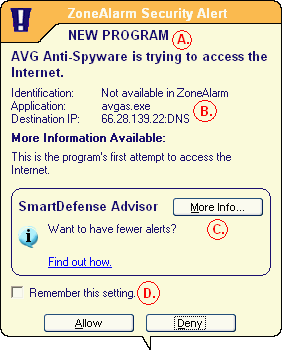
A. Displays the name of the program trying to access the Internet. If you do not recognise this name, do not allow it until you know more about the program.
B. Gives you more details about the program and where it is heading. avgas.exe is the name of the executable file trying to access the Internet in this example.
C. When you click on the More Info... button, you will be taken to the ZoneAlarm website giving you more details about the program trying to access the Internet.
D. This is the "Remember" setting mentioned earlier on this page. Tick this box to make ZoneAlarm remember your decision and ZoneAlarm will not ask you again about this specifc activity or program.
If you do not have a firewall installed on your computer, we recommend that you download the free version of ZoneAlarm. The free version is fairly easy to use and won't confuse you with too many options. If you are interested in a more advanced firewall, refer to the Firewalls section on our Cyber Security Software page. Instead of buying a stand-alone firewall application, you may want to consider buying an Internet Security Suite. Fans of AVG can buy AVG Professional bundled with a built-in firewall.